Virtual Private Cloud (VPC)¶
A virtual private cloud (VPC) is a secure and isolated private cloud infrastructure hosted within a public cloud. You can use a VPC to restrict public access to web services. For example, you can have a web service connect to its database service via a private network, but still be accessible from a public network. This way, a VPC creates an additional layer of security and control.
In SolusVM 2, you can configure a VPC for yourself as well as offer it to your users.
알려진 문제 및 제한 사항¶
At the moment, the following limitations exist:
- Only KVM virtual servers support the VPC feature.
- For security reasons, you can't use a VPC if your compute resources have only public IP addresses. We're planning to remove this restriction in the future to allow a VPC for such compute resources as well. Meanwhile, you can use WireGuard to create tunnels between compute resources over a public network and then use the WireGuard interface IP address as the SolusVM 2 "IP for VPC networks" setting.
- It's impossible to create a virtual server without a public IP address and with a VPC only.\ We're planning to remove this restriction in the future.\ We're planning to remove this restriction in the future.
The VPC feature also has some aspects worth mentioning:
- In SolusVM 2, a VPC is a location-bound feature.
- All virtual servers created in SolusVM 2 and attached to a VPC use the Open vSwitch (OVS) technology, while those created in SolusVM 1, Linux bridge. If you migrate VPC-attached servers from SolusVM 1 to SolusVM 2, the latter automatically changes the type of the migrated servers to Open vSwitch.
VPC Configuration Overview¶
The usual process of providing a VPC for users' virtual servers consists of the following steps:
- You create a VPC in the Administrator Area.
- You grant users the VPC-related permissions.
- Users attach their servers to the created VPC.
We'll break down each step in more detail below.
Creating a VPC¶
To create a VPC network:
-
Go to Compute Resources.
-
Choose a compute resource that will offer a VPC.
메모
Make sure the compute resource is only related to one [location](../billing-integration-guide/prepaid-billing/Configurable-options/Locations.md). Otherwise, when necessary, SolusVM 2 will pick the location with the highest ID. -
Click the
 icon next to the compute resource of your choice.
icon next to the compute resource of your choice. -
In the "Network" section, under "IP for VPC network", specify a private IPv4 address which belongs to one of the following ranges:
10.0.0.0 – 10.255.255.255 (10.0.0.0/8 prefix) 172.16.0.0 – 172.31.255.255 (172.16.0.0/12 prefix) 192.168.0.0 – 192.168.255.255 (192.168.0.0/16 prefix)
-
Go to Network > VPC Networks, and then click Create VPC Network.
-
Give your VPC network a recognizable name.
-
Choose the network's list type. The type defines the way IP addresses will be assigned to the VPC network:
- To allocate a range of private IP addresses (for example, 10.1.1.1 – 10.1.1.7), select "Range".
- To assign individual private IP addresses in a random order (for example, 10.1.1.1 and 10.1.1.6), select "Set".
-
If you've selected "Range" in the previous step, specify a range of private IP addresses. If you've selected "Set", there's no need to do that. Users will later add individual private IP addresses for this VPC network in the User Area.

-
Specify the IP addresses' netmask.
-
Select the location of the VPC network.
-
Specify the email address of the network owner. You can create a VPC network for yourself or another user.
-
저장을 클릭합니다.
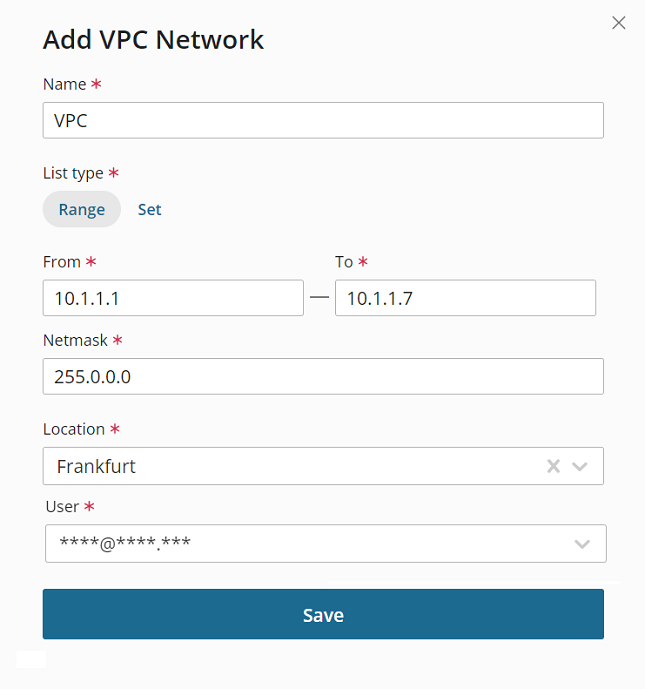
You've created a VPC network. If you've created it for yourself, you got the job done. If you've created it for another user, you need to make sure they have the required permissions.
VPC-Related Permissions¶
The VPC feature introduces the following permissions:
- manage all VPC networks
- manage owned VPC networks
- get VPC networks
The "manage all VPC networks" permission should be reserved only for the Administrator role.
With the "manage owned VPC networks" permission, a user can create their own VPC network and also attach and detach virtual servers from it.

With the "get VPC networks" permission, a user can see VPC networks created and attached to their virtual servers by you. They can neither create their own VPC networks nor detach those created by you from their virtual servers.

Without any VPC permissions granted, a user can still see private IP addresses from the VPC network but can't see which VPC network has provided these IP addresses.

Usually, you choose to grant the "manage owned VPC networks" and "get VPC networks" permissions. The "Client" role doesn't have them enabled by default, and you cannot edit the role because it's built-in.
You will need to create a new role with a set of permissions related to a VPC, and then assign this role to one or multiple users.
To grant users the permissions to use the VPC network:
-
액세스 > 역할로 이동한 다음 역할 추가를 클릭합니다.
-
역할에 알아보기 쉬운 이름을 지정하십시오.
-
Select the "manage owned VPC networks" and "get VPC networks" permissions.

-
저장을 클릭합니다.
-
액세스 > 사용자로 이동합니다.
-
새 역할을 부여하려는 사용자 옆에 있는
 아이콘을 클릭하세요.
아이콘을 클릭하세요. -
'역할'에서 기본 '클라이언트' 역할을 유지한 다음 생성한 새 역할을 선택합니다.
-
저장을 클릭합니다.
The user now has the necessary permissions.
역할 및 권한 생성 및 사용에 대해 자세히 알아보세요.
Attaching Servers to the VPC in the User Area¶
If you've granted the "manage owned VPC networks" and "get VPC networks" permissions, users can now attach and detach their virtual servers from the VPC. They can do so while editing already existing servers.
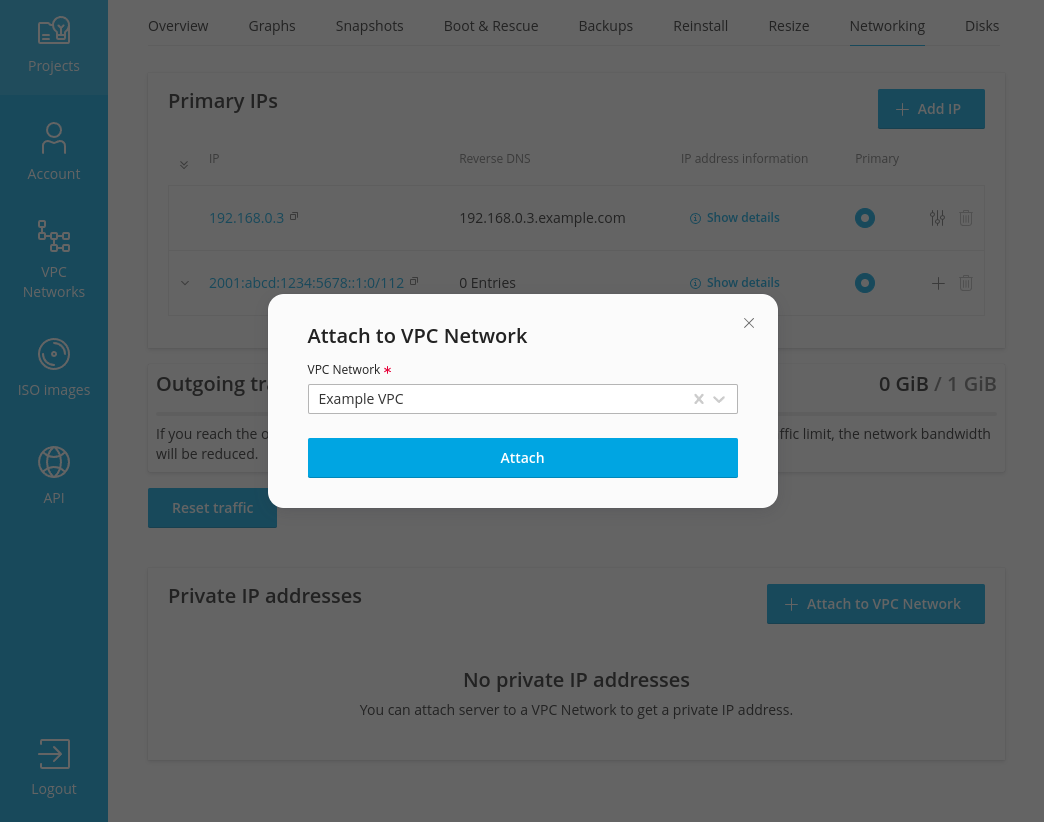
They can also attach a new server to the VPC when they create the server.
